Ransomware has been around for many years. The evolution of its capabilities and implementation has accelerated its impact on contemporary society. Governmental agencies and cybercrime groups have been involved in this cat-and-mouse game for quite some time, and the reality is that this game will not end anytime soon.
In the beginning of 2024, the FBI announced a major blow to one of the biggest cybercrime groups in the field: LockBit. The following will provide a brief overview of the history of ransomware, how LockBit became a prominent player and what companies can do to reduce the probabilities of becoming a victim or deal with it effectively if they become a victim.
The history of ransomware
Ransomware has changed significantly since its first recognised occurrence in 1989. Back then, the ‘AIDS’ malware (i.e. trojan horse) was executed through a floppy disk, encrypting the filenames on drive C:. Around 26,000 floppy disks were reportedly distributed to 90 countries. It’s creator, evolutionary biologist Joseph L. Popp, was associated with supporting research on AIDS. Fortunately, no one on the mailing list (attendees of the World Health Organization’s international AIDS conference) is known to have paid for the extortion.
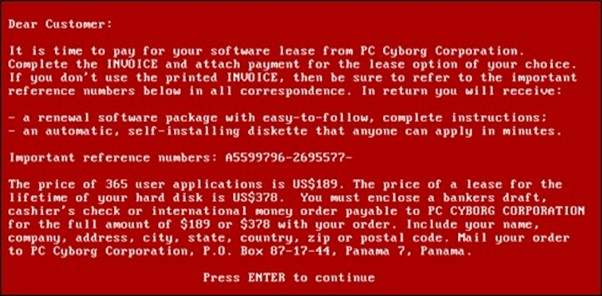
Figure 1 – The text prompt shown after infection, by Joseph L. Popp, AIDS Information Trojan author (Public Domain).
Certain versions of the malware bore resemblance to a logic timebomb, given that it encrypted the hard drive after 90 reboots. Affected users were then confronted with a text message asking for a payment of at least $189, - to a fictional company. This first type of ransomware made use of simple symmetric encryption and the decryption key could be extracted from the code of the trojan.
Evolution
With the internet becoming more widely available, so did ransomware. Instead of symmetric encryption, newer kinds of trojans were employing more sophisticated and asymmetric RSA encryption methods, along with increasing key sizes. Next to the internet, other technologies like the emergence of the blockchain and onion routing (onion routing is a technique for anonymous communication over a computer network. In an onion network, messages are encapsulated in layers of encryption, analogous to the layers of an onion) facilitated the effectiveness of ransomware attacks. Cryptocurrency demands undermine traceability and the existence of crypto mixers assist in money laundering. Additionally, anonymous communication through Tor makes it easier to stay under the radar.
A game changer appeared in 2013 when Cryptolocker came to the fore. This ransomware was the first to be spread through a botnet, and used 2048-bit RSA encryption to increase its reach and complexity.
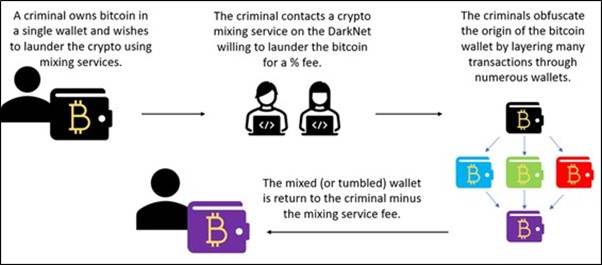
Figure 2 - An example of how crypto mixing facilitates money laundering (Creative Commons).
In the last decade, the scale and frequency of ransomware attacks have increased significantly, especially since 2020. There are several reasons for this trend. Firstly, Ransomware-as-a-service (RaaS) became a phenomenon, implying a branching-off in operations: different groups (‘brokers’) specialised and became responsible for different aspects of the cyber kill chain. This created a market in which specialised groups cooperate and compete with each other. In effect, this marketisation by RaaS programmes accelerates the development of sophisticated ransomware, including user dashboards, subscriptions, and even technical support. This, in turn, allows affiliates (including those without technical knowledge) to purchase and execute ransomware quicker and more efficiently than before, contributing to the growing frequency and impact of corresponding attacks.
Incidentally, in 2017 a hacker group named The Shadow Brokers leaked high-grade hacking tools that were developed by the NSA. One of these tools, EternalBlue, made it possible for malicious authors to infect many systems worldwide.
Ransomware initially threatened its victims to pay in order to unlock their data. However, the existence of (offline) backups allows companies to regain business continuity without having to pay the ransomware operators. This fact undoubtedly encouraged these operators to shift to another strategy: public leaking of sensitive data. Given that companies are bound by privacy laws, incurring penalties by failure to comply (and have a reputation to take seriously), this strategy provides ransomware operators in the RaaS market with a renewed leverage (double extortion) for their blackmailing campaigns.
LockBit
From 2019 onwards, LockBit has evolved as the most prolific RaaS group in the market. According to Flashpoint, 21 percent of worldwide ransomware attacks in 2023 were attributable to LockBit’s ransomware. Initially appearing as LockBit 1.0 or “ABCD” (where encrypted files received an ’.abcd’ extension), the malware developed to its current (2024) version, namely LockBit-NG-Dev (LockBit 4.0).
Several reasons are recognised for its infamous rise to the top of the game. One such reason is its business-oriented approach, including a ‘bug bounty’ programme for internal and external innovation, a clear and generous affiliate programme, and taking into account data privacy laws applying to its targets, so as to maximise its potential revenue. Another is the fall of other notable cybercrime groups (e.g. Conti in 2022), which created more traction for LockBit. Just as important is the continuous development of its ransomware, including technical features like faster encryption and with the latest iteration, functionality that randomises file names to frustrate restoration.
Takedown
In February 2024, a collective operation led by the UK’s National Crime Agency (UK NCA) and the US’s FBI, culminated in a disruption of LockBit operations. This included a takedown of 34 servers, a freeze of 200 cryptocurrency accounts, several arrests and a takeover of a large data set that will be used in further investigations. UK NCA used this opportunity to ‘deface’ LockBit’s leak site (see the figure below).
However, the alleged leader of LockBit, LockBitSupp, responded to the operation and attempted to downplay its impact. Even though a new version of LockBit has entered the scene, it is hard to predict the extent to what extent LockBit will retain its position, especially given its recognised problems even before the takedown. In any case, cybercrime groups and the businesses are intertwined in a continued cycle of co-evolution, which means that it is never a bad idea to take cyber maturity and resilience seriously.
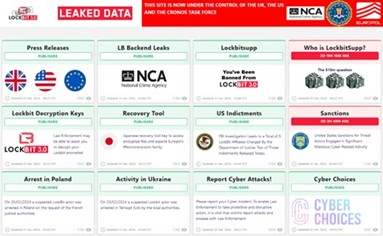
Figure 3 - The seizure of the LockBit leak site as part of Operation Cronos.
Reduce risk or deal with it
Businesses can take many steps to reduce the risk of becoming a ransomware victim. Given the evolution of ransomware gangs and their methods, this should be on top of any company’s priority list. Risk reduction is multi-faceted and consists of measures and controls pertaining to people, technology and processes. In the case of ransomware, initial entry most often occurs through phishing emails that contain malicious links or attachments. At first glance, this justifies a focus on the people side of risk reduction. This means that awareness campaigns are generally considered an important first step. However, this is not a cure-all, and the reality is that attackers only need to find one vulnerability or phishing victim, while defenders need to keep the whole infrastructure protected. What to do when ransomware has entered the building?
Deal with it
This is where Sopra Steria comes in. Apart from our cybersecurity & compliance solutions in order to keep malicious actors out, we also want to make sure that your business has effective ways of dealing with malicious actors when they are in. We live in a world that is increasingly becoming more digital (consider the current developments of AI and Internet of Things (IoT). This means that it becomes more difficult to defend and manage your attack surface. Therefore, we believe that the Assume Breach mindset is the right stance.
Sopra Steria assists companies by advising on effective methods of incident response. This can translate to assistance with setting up a proper information security management system (ISMS) or tabletop cyber crisis simulations. A ransomware simulation can turn out to be rather effective because it is a hands-on approach in which your business is confronted with a ‘pressure cooker’ that reflects the pressure of a real attack. Aiming to test and improve both your strategic and operational resiliency, several questions can be factored in.
Are the incident urgency and business impact clearly defined? Who is to communicate with the press, and when? Is there a plan for business continuity in place? What about your supply chain? Questions like these should be asked and Sopra Steria is happy to help you out answering them.
Interested to know more about our approach and finding out how we can help improve your security posture?
Feel free to contact Helmer Berkhoff (Practice Lead Security Operations & IAM) for more information: helmer.berkhoff@soprasteria.com
Author: Brandon Pakker
Technical Security Consultant